-
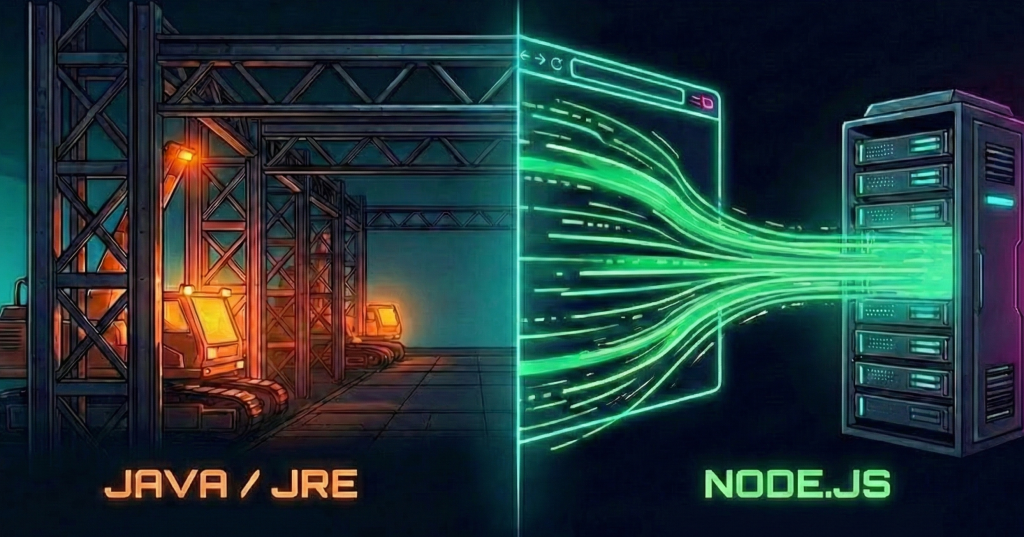
Two Runtimes, One Computer
The author explores the necessity of Node.js as a runtime environment for JavaScript, comparing it to Java’s JRE. They highlight the different functionalities of both environments, showcasing that while both…
-
AI Model Taxonomy
Right … AI acronyms. I started off looking at LLMs (Large Language Models), but now I also look at SLMs, LAMs, VLAs, and MoEs. Are these just marketing buzzwords? Sometimes.…
-
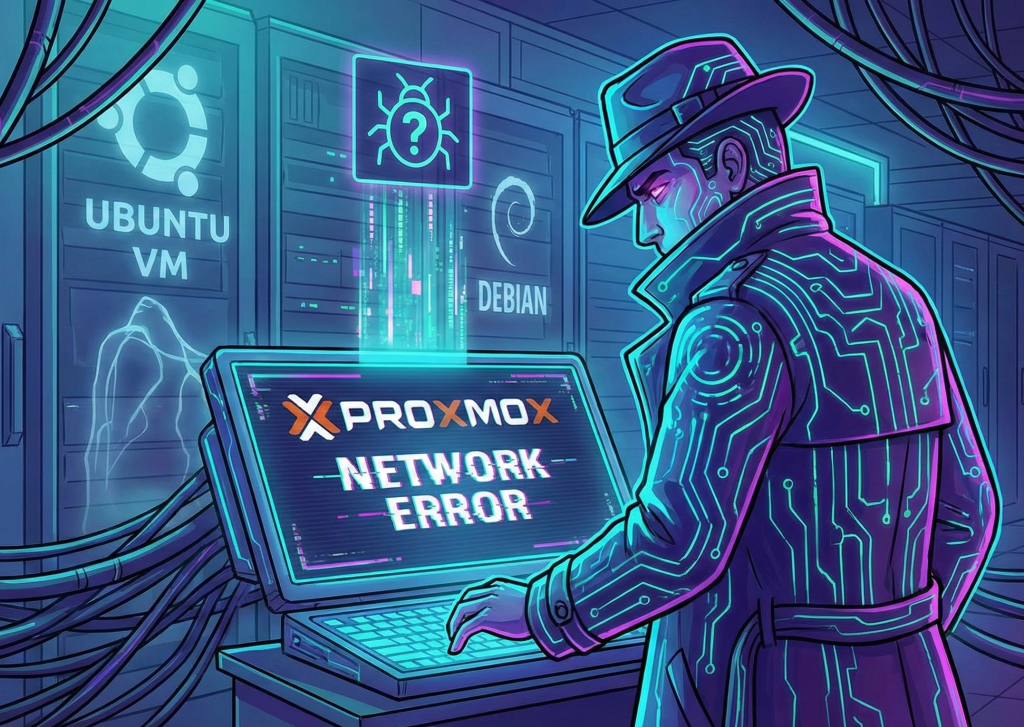
Troubleshooting: Buddies with AI
The Case of the Phantom Network Bug: A Proxmox Troubleshooting Journey TL;DR: If your Ubuntu/Debian VM installs are failing on Proxmox 8.1 specifically when the network is enabled, stop debugging…
-
Quick Ref Guide on AI
Component Layer Human Readable Role Technical Term Definition 1. The Brain The Engine Foundation Model (LLM) The core model (like Claude or Titan) pre-trained on public data that handles logic…
-
Windows Logon Types
Type Name Scenario & Description Investigator Note 0 System Used only by the System account during startup. You generally ignore this unless investigating boot-level persistence. 2 Interactive A user logging…
-
A Glossary of Terms : Attacks
A Quick Glossary of Attack Types